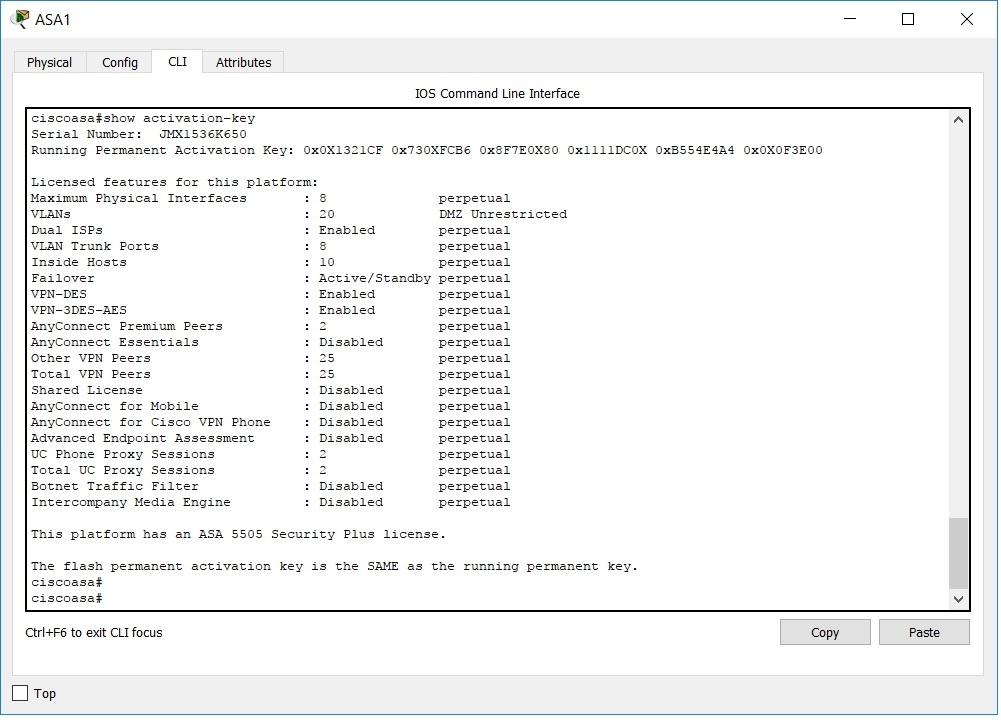
Cisco Asa Activation Key Gns3 2017 And Software
Who ever want to know if there is key generator for ASA 'Forget About It' every ASA is different so the serial is generated by Device bases. This is how it`s done Cisco will ask you to provide the serial of your ASA Device and from there you will get a Key from Cisco. If there is a ASA keygen i would love to know about it when i sleep. How-To: ASA in GNS3 with ASDM. They also recommend that you use the ASAv directly from Cisco’s VIRL software. A google search will get you the image you need. Next, you need to configure the ASAv to get an IP address via DHCP and also activate the http server on the ASA and allow the IP that you get from DHCP to access the http server. So upon reload we will check the license status with sh activation-key. ( PAT ) using Cisco ASA in GNS3. Site to Site VPN using Cisco ASA Firewall ( software.
- Cisco Asa Activation Key Gns3 2017 And Software Download
- Cisco Asa Activation Key Gns3 2017 And Software Downloads
- WARNING ASA 8 IS NOT SUPPORTED. You may find a lot of tutorials on the Internet explaining how to extract ASA 8 images from physical hardware devices and use them with GNS3. This method was the only way to get an ASA image in the past, but the results are random; and getting worse with modern computers and operating systems.
- GNS3 - Initial Setup, Adding Routers, Hosts, and ASA Firewalls. Adding a Cisco ASA to GNS3. To add them you need to change the ASA’s activation key.
This is the fourth from the series of the articles that discuss configuration of the enterprise network. The article explains configuration of the device ASAv-I. The device is a Cisco Adaptive Security Virtual Appliance (ASAv) version 9.6(1) installed on qcow2 Qemu disk. The ASAv-I provides traffic filtering and inspection services for the campus network and Data Center (DC). It also connects the campus network and DC to the vIOS-EDGE-I edge router.
Picture 1 - ASAv-I, Campus, DC and Edge Connection
Note: The recommended RAM size for ASAv instance is 2048 MB. In order to lower memory consumption, GNS3 is configured to assign 1536 MB to the ASAv.
Note: The interface eth0 on the ASAv-I is referred as the interface Management0/0 in ASAv configuration. The interface eth0 is not connected as we use the inside interfaces for management instead. The first connected interface is then the interface eth1 that is referred as the interface GigabitEthernet0/0 in ASAv CLI. Similarly, the second connected interface eth2 is referred as the GigabitEthernet0/1 and so on.
Note: Here is the configuration file of vASA-I.
ASAv-I Configuration
Once we start ASAv, the Qemu window is launched. However we want to use GNS3 console instead of Qemu console. Therefore we need to redirect vASA output to a serial port. When ASAv boots up, copy the file coredump.cfg to a disk0 in a privileged exec mode (password is not set). Then reboot the ASAv and you should be able to manage ASAv via GNS3 console afterwards.
# copy disk0:/coredumpinfo/coredump.cfg disk0:/use_ttyS0
As a first step we configure the hostname.
ciscoasa> en
ciscoasa# conf t
ciscoasa(config)# hostname ASAv-I
1. Interfaces Configuration
The links connecting ASAv-I to the Core switches are configured with the interface name INSIDE0 and INSIDE1. They have assigned a security level 100. The links connecting ASAv-I to the DC are configured with the interface name SERVER0 and SERVER1. They have assigned a security level 50. The link connecting the ASAv-I to the vIOS-EDGE-I router is configured with the interface name OUTSIDE and it has assigned a security level 0.
Thanks to the security levels concept, TCP and UDP traffic from the hosts connected to the inside interfaces (level 100) can reach hosts in DC, behind the server interfaces (level 50) or hosts in the Internet behind the outside interface (level 0). The same is valid for traffic sent from DC to the Internet. In this case, network traffic takes a path from the server interface (level 50) to the outside (level 0) interface and back.
In general, traffic initialized from the interface with a higher security level is allowed to enter the interface with a lower security level and back. However traffic initialized from the interface with a lower security level is not passed to the interface with a higher security level. For this reason traffic initialized behind the outside interface is passed neither to the inside nor to the server interfaces. If we need to allow traffic initialized from host connected to the outside interface (level 0) to enter the interfaces with a higher level (100 or 50, in our case), we have to configure an access-list (ACL). The ACL must explicitly allow particular network traffic (e.g. TCP, UDP or ICMP) to enter the outside interface.
ASAv-I(config)# interface Gi0/0
ASAv-I(config-if)# description Link to vIOS-Core-II
ASAv-I(config-if)# nameif INSIDE0
ASAv-I(config-if)# security-level 100
ASAv-I(config-if)# ip address 172.16.0.13 255.255.255.252
ASAv-I(config-if)# no shutdown
ASAv-I(config-if)# exit
ASAv-I(config)# interface Gi0/1
ASAv-I(config-if)# description Link to vIOS-Core-I
ASAv-I(config-if)# nameif INSIDE1
ASAv-I(config-if)# security-level 100
ASAv-I(config-if)# no shutdown
ASAv-I(config-if)# exit
ASAv-I(config)# interface Gi0/2
ASAv-I(config-if)# description Link to vIOS-EDGE-I
ASAv-I(config-if)# nameif OUTSIDE
ASAv-I(config-if)# security-level 0
ASAv-I(config-if)# ip address 172.16.0.1 255.255.255.252
ASAv-I(config-if)# no shutdown
ASAv-I(config-if)# exit
ASAv-I(config)# interface Gi0/3
ASAv-I(config-if)# description Link1 to vIOS-Ser-I
ASAv-I(config-if)# nameif SERVER0
ASAv-I(config-if)# security-level 50
ASAv-I(config-if)# ip address 172.16.0.5 255.255.255.252
ASAv-I(config-if)# no shutdown
ASAv-I(config-if)# exit
ASAv-I(config)# interface Gi0/4
ASAv-I(config-if)# description Link2 to vIOS-Ser-I
ASAv-I(config-if)# nameif SERVER1
ASAv-I(config-if)# security-level 50
ASAv-I(config-if)# ip address 172.16.0.17 255.255.255.252
ASAv-I(config-if)# no shutdown
ASAv-I(config-if)# exit
2. Logging Configuration
Enable Logging messages to console, RAM (buffer) and VTY session and configure appropriate logging levels.
ASAv-I(config)# logging enable
ASAv-I(config)# logging console 6
ASAv-I(config)# logging buffered 6
ASAv-I(config)# logging monitor 6
Configure syslog server server and syslog level 5 - notifications.
ASAv-I(config)# logging host SERVER0 172.16.50.1
ASAv-I(config)# logging trap notifications
Note: SERVER0 is the interface name.
Turn on monitoring logs on VTY session.
ASAv-I# terminal monitor
Note: Use command terminal no monitor to turn off displaying logs on VTY session.
Set exec timeout to 0 - you will never be disconnected from console.
ASAv-I(config)# console timeout 0
3. Default Static Route Configuration
We need to configure a default static route in order to reach hosts in the Internet. This route will be later redistributed to the OSPF process.
ASAv-I(config)# route OUTSIDE 0.0.0.0 0.0.0.0 172.16.0.2
4. Objects and Object Groups Configuration
Cisco Asa Activation Key Gns3 2017 And Software Download
Using objects and object groups are reusable components that help to maintain configuration. We can modify an object in one place and have it be reflected in all other places that are referencing it.
ASAv-I(config)# object network vlan10_192.168.10
ASAv-I(config-network-object)# subnet 192.168.10.0 255.255.255.0
ASAv-I(config)# object network vlan20_192.168.20
ASAv-I(config-network-object)# subnet 192.168.20.0 255.255.255.0
ASAv-I(config)# object network vlan30_192.168.30
ASAv-I(config-network-object)# subnet 192.168.30.0 255.255.255.0
ASAv-I(config)# object network vlan40_192.168.40
ASAv-I(config-network-object)# subnet 192.168.40.0 255.255.255.0
ASAv-I(config)# object network vlan50_172.16.50
ASAv-I(config-network-object)# subnet 172.16.50.0 255.255.255.0
ASAv-I(config)# object network google_dns1
ASAv-I(config-network-object)# host 8.8.8.8
ASAv-I(config)# object network google_dns2
ASAv-I(config-network-object)# host 8.8.4.4
ASAv-I(config)# object network server1
ASAv-I(config-network-object)# host 172.16.50.1
ASAv-I(config)# object network vios-l3
ASAv-I(config-network-object)# host 10.1.1.5
ASAv-I(config)# object network loopbacks
ASAv-I(config-network-object)# subnet 10.1.1.0 255.255.255.0
ASAv-I(config)# object-group network mgmt
ASAv-I(config-network-object-group)# network-object object vlan40_192.168.40
ASAv-I(config)# object-group network end_vlans
ASAv-I(config-network-object-group)# network-object object vlan10_192.168.10
ASAv-I(config-network-object-group)# network-object object vlan20_192.168.20
ASAv-I(config-network-object-group)# network-object object vlan30_192.168.30
ASAv-I(config-network-object-group)# network-object object vlan40_192.168.40
ASAv-I(config)# object-group network server_vlans_all
ASAv-I(config-network-object-group)# description All server VLANs
ASAv-I(config-network-object-group)# network-object object vlan50_172.16.50
ASAv-I(config)# object-group network google_dns
ASAv-I(config-network-object-group)# network-object object google_dns1
ASAv-I(config-network-object-group)# network-object object google_dns2
vASA-I(config)# object-group service server1_tcp_out tcp
vASA-I(config-service-object-group)# port-object eq http
vASA-I(config-service-object-group)# port-object eq https
vASA-I(config-service-object-group)# port-object eq domain
vASA-I(config)# object-group service server1_udp_out udp
vASA-I(config-service-object-group)# port-object eq ntp
vASA-I(config-service-object-group)# port-object eq domain
5. Management Protocol Configuration
5.1 ICMP ECHO Request and Echo Reply Messages on Inside Interfaces
Allow management (192.168.40.0/24), server (172.16.50.0/24) and loopback (10.1.1.0/24) subnets to ping the ASA inside interfaces.
ASAv-I(config)# icmp permit 192.168.40.0 255.255.255.0 INSIDE0
ASAv-I(config)# icmp permit 192.168.40.0 255.255.255.0 INSIDE1
ASAv-I(config)# icmp permit 172.16.50.0 255.255.255.0 SERVER0
ASAv-I(config)# icmp permit 172.16.50.0 255.255.255.0 SERVER1
ASAv-I(config)# icmp permit 10.1.1.0 255.255.255.0 INSIDE0
ASAv-I(config)# icmp permit 10.1.1.0 255.255.255.0 INSIDE1
5.2 SSH Access
ASAv-I(config)# username admin password cisco
ASAv-I(config)# aaa authentication ssh console LOCAL
ASAv-I(config)# crypto key generate rsa modulus 4096
Allow SSH access to INSIDE0 and INSIDE1 interfaces.
ASAv-I(config)# ssh 192.168.40.0 255.255.255.0 INSIDE0
ASAv-I(config)# ssh 192.168.40.0 255.255.255.0 INSIDE1
Set timeout for ssh session. Timeout is set to maximum value 60 minut.
ASAv-I(config)# ssh timeout 60
6. OSPF Protocol and Authentication Configuration
The OSPF routing protocol ensures that connectivity is between campus and DC. The static default route pointing to vIOS-EDGE-I is redistributed to OSPF process. Authentication with MD5 algorithm is used in order to prevent peering with a rouge OSPF router.
ASAv-I(config)# router ospf 1
ASAv-I(config-router)# router-id 1.1.1.3
ASAv-I(config-router)# network 172.16.0.4 255.255.255.252 area 0
ASAv-I(config-router)# network 172.16.0.8 255.255.255.252 area 0
ASAv-I(config-router)# network 172.16.0.12 255.255.255.252 area 0
ASAv-I(config-router)# network 172.16.0.16 255.255.255.252 area 0
ASAv-I(config-router)# default-information originate
ASAv-I(config-router)# exit
ASAv-I(config)# interface GigabitEthernet 0/0
ASAv-I(config-if)# ospf authentication message-digest
ASAv-I(config-if)# ospf message-digest-key 1 md5 #MyPass!034
ASAv-I(config)# interface GigabitEthernet 0/1
ASAv-I(config-if)# ospf authentication message-digest
ASAv-I(config-if)# ospf message-digest-key 1 md5 #MyPass!034
ASAv-I(config)# interface GigabitEthernet 0/3
ASAv-I(config-if)# ospf authentication message-digest
ASAv-I(config-if)# ospf message-digest-key 1 md5 #MyPass!034
ASAv-I(config)# interface GigabitEthernet 0/4
ASAv-I(config-if)# ospf authentication message-digest
ASAv-I(config-if)# ospf message-digest-key 1 md5 #MyPass!034
7. Zone Configuration
The ASAv-I installs only one route to the subnets: 192.168.x.0/24, 10.0.0.x/30 even they are two paths to these routes available. The first path is via vIOS-Core-I (172.16.0.10) and the second path is via vIOS-Core-II (172.16.0.14). It is because ECMP is not supported across multiple interfaces, so we cannot define a route to the same destination on a different interface. However, with zones, we can have up to 8 equal cost static or dynamic routes across up to 8 interfaces within a zone. To achieve ECMP via two different interfaces, we will create a zone inside_zone and assign Gi0/0 and it Gi0/1 to this zone.
ASAv-I(config)# zone inside_zone
ASAv-I(config)# interface gigabitEthernet 0/0
ASAv-I(config-if)# zone-member inside_zone
ASAv-I(config)# interface gigabitEthernet 0/1
ASAv-I(config-if)# zone-member inside_zone
Similarly, we will create zone server_zone for Gi0/3 and Gi/04.
ASAv-I(config)# zone server_zone
ASAv-I(config)# interface gigabitEthernet 0/3
ASAv-I(config-if)# zone-member server_zone
ASAv-I(config)# interface gigabitEthernet 0/4
ASAv-I(config-if)# zone-member server_zone
Picture 2 - OSPF Routes
8. Access Lists (ACLs) Configuration
8.1 Access List out-to-ins
Permit ICMP Echo Reply packets with the source IP address 8.8.8.8 and 8.8.4.4 to end user subnets 192.168.x.0/24. The ACL allows users to check connectivity to Google public DNS with the ping command. Without the access-list, vASA does not pass ICMP Echo Reply packets from the interface outside to the interface inside or server.
ASAv-I(config)# access-list out-to-ins extended permit icmp object-group google_dns object-group end_vlans echo-reply
Permit ICMP Echo Reply packets with any source IP address to MGMT (192.168.40.0/24), Vlan50 (172.16.50.0/24) and loopback's IP 10.1.1.0/24 subnets.
ASAv-I(config)# access-list out-to-ins extended permit icmp any object-group mgmt echo-reply
ASAv-I(config)# access-list out-to-ins extended permit icmp any object loopbacks echo-reply
ASAv-I(config)# access-list out-to-ins extended permit icmp any object vlan50_172.16.50 echo-reply
Note: The other way to allow ICMP Echo Reply packets to enter the outside interface is to enable ICMP inspection on ASAv. In this case, the ASAv dynamically allows the corresponding ICMP ECHO Reply to pass through without needing to have access-list. However we do not want all devices in campus or DC to be able ping hosts in the Internet. For this reason we have shown ACL method.
Permit DNS request/reply from 8.8.8.8 and 8.8.4.4 from/to Server1 - 172.16.50.1.
ASAv-I(config)# access-list out-to-ins permit udp object-group google_dns object server1 eq 53
Permit NTP request from vIOS-L3 (10.1.1.5) to Server1.
ASAv-I(config)# access-list out-to-ins permit udp object vios-l3 object server1 eq 123
Permit syslog (UDP 514) traps from vIOS-L3 (10.1.1.5) to Server1.
ASAv-I(config)# access-list out-to-ins permit udp object vios-l3 object server1 eq 514
Apply ACL out-to-ins to the interface Outside in inbound direction.
ASAv-I(config)# interface gi0/2
ASAv-I(config-if)# access-group out-to-ins in interface OUTSIDE
8.2 Access List dc-to-ins_out
Permit hosts in subnet (172.16.50.0/24) to send traffic to any IP address, the destination TCP port 80 (http),443 (https) and 53 (DNS).
vASA-I(config)# access-list dc-to-ins_out extended permit tcp object vlan50_172.16.50 any object-group server1_tcp_out
Permit hosts in subnet (172.16.50.0/24) to send traffic to any IP address, the destination UDP port 123 (NTP) and 53 (DNS).
vASA-I(config)# access-list dc-to-ins_out extended permit udp object vlan50_172.16.50 any object-group server1_udp_out
Permit hosts in subnet (172.16.50.0/24) to send to ICMP Echo Request (ping) to any IP address to the IP addresses 8.8.8.8 and 8.8.4.4.
vASA-I(config)# access-list dc-to-ins_out extended permit icmp object vlan50_172.16.50 object-group google_dns echo
Permit hosts in mgmt VLAN40 (192.168.40.0/24) to ping Server1.
vASA-I(config)# access-list dc-to-ins_out extended permit icmp object vlan50_172.16.50 object vlan40_192.168.40 echo-reply
Apply ACL dc-to-ins to the interfaces SERVER0 and SERVER1 in inbound direction.
vASA-I(config)# access-group dc-to-ins_out in interface SERVER0
vASA-I(config)# access-group dc-to-ins_out in interface SERVER1
Picture 3 - Access-Lists
9. NTP Configuration
ASAv-I(config)# ntp server 172.16.50.1
ASAv-I(config)# clock timezone UTC+2 +2
Picture 4 - Checking NTP Associations
10. Radius Server Configuration
10.1 Create Local User
Create a local user with full access in case Radius servers is not reachable.
ASAv-I(config)# username admin password cisco privilege 15
We also set password for privileged exec mode.
ASAv-I(config)# enable password cisco
Now Activate AAA.
Usb serial emulation driver uni directional antennas 2017. vIOS-Core-I(config)# aaa new-model
10.2 Radius Server
The RADIUS server and a vASA use a shared secret text string to encrypt passwords and exchange responses.To configure RADIUS to use the AAA security commands, we must specify the host running the RADIUS server daemon and a secret text (key) string that it shares with the ASAv.
ASAv-I(config)# aaa-server Server1 protocol radius
ASAv-I(config-aaa-server-group)# exit
ASAv-I(config)# aaa-server Server1 (SERVER0) host 172.16.50.1 test123
ASAv-I(config-aaa-server-host)# key test123
ASAv-I(config-aaa-server-host)# authentication-port 1812
ASAv-I(config-aaa-server-host)# accounting-port 1813
10.3 Authentication for Access to Serial Console
If all servers in the server group have been deactivated, authentication will be done against the local database.
ASAv-I(config)# aaa authentication serial console Server1 LOCAL
10.4 Authentication for Access via SSH
ASAv-I(config)# aaa authentication ssh console Server1 LOCAL
10.5 Authentication for Access to Privileged Exec Mode (Enable)
ASAv-I(config)# aaa authentication enable console Server1 LOCAL
Transition a failed AAA server to Active.
ASAv-I(config)# aaa-server Server1 active host 172.16.50.1
Picture 5 - Checking AAA Server
11. Application Inspection Configuration
We also need to inspect network traffic on application layer to check both Layer 7 header and the payload of the segments to ensure that packets do not carry harmful content. To add http inspection to the list of default inspected applications, we will create an optional policy-map type http named http_map. In case of http protocol violation, TCP traffic is dropped.
ASAv-I(config)# policy-map type inspect http http_map
ASAv-I(config-pmap)# parameters
ASAv-I(config-pmap-p)# protocol-violation action drop-connection log
Note: class-maps identify traffic, actions are assigned with policies (policy-map), and then the service policies are activated on interfaces (service-policy).
Assign our http_map policy to the global_policy map.
ASAv-I(config)# policy-map global_policy
ASAv-I(config-pmap)# class inspection_default
ASAv-I(config-pmap-c)# inspect http http_map
ASAv-I(config)# service-policy global_policy global
Check inspected protocols in running-config.
Picture 6 - Checking Inspected Application Protocols
To show statistic of service-policy inspect for a particular application protocol, use the command below. The command shows statistic for DNS protocol.
Picture 7 - DNS Inspection Statistics
Cisco has released free software updates that address the vulnerability described in this advisory. Customers may only install and expect support for software versions and feature sets for which they have purchased a license. By installing, downloading, accessing, or otherwise using such software upgrades, customers agree to follow the terms of the Cisco software license:
http://www.cisco.com/en/US/docs/general/warranty/English/EU1KEN_.html
Additionally, customers may only download software for which they have a valid license, procured from Cisco directly, or through a Cisco authorized reseller or partner. In most cases this will be a maintenance upgrade to software that was previously purchased. Free security software updates do not entitle customers to a new software license, additional software feature sets, or major revision upgrades.
When considering software upgrades, customers are advised to regularly consult the advisories for Cisco products, which are available from the Cisco Security Advisories and Alerts page, to determine exposure and a complete upgrade solution.
In all cases, customers should ensure that the devices to be upgraded contain sufficient memory and confirm that current hardware and software configurations will continue to be supported properly by the new release. If the information is not clear, customers are advised to contact the Cisco Technical Assistance Center (TAC) or their contracted maintenance providers.
Customers Without Service Contracts
Customers who purchase directly from Cisco but do not hold a Cisco service contract and customers who make purchases through third-party vendors but are unsuccessful in obtaining fixed software through their point of sale should obtain upgrades by contacting the Cisco TAC:
http://www.cisco.com/en/US/support/tsd_cisco_worldwide_contacts.html
Customers should have the product serial number available and be prepared to provide the URL of this advisory as evidence of entitlement to a free upgrade.
Fixed Releases
In the following table, the left column lists major releases of Cisco ASA Software. The right column indicates whether a major release isaffected by the vulnerability described in this advisory and the first release that includes the fix for this vulnerability.
Cisco Asa Activation Key Gns3 2017 And Software Downloads
| Cisco ASA Software Major Release | First Fixed Release |
|---|---|
| Prior to 9.01 | Affected, migrate to 9.1(7.7) or later |
| 9.01 | Affected, migrate to 9.1(7.7) or later |
| 9.1 | 9.1(7.7) or later |
| 9.2 | 9.2(4.11) or later |
| 9.31 | Affected, migrate to 9.4(4) or later |
| 9.4 | 9.4(4) or later |
| 9.5 | 9.5(3) or later |
| 9.6 | 9.6(1.5) or later |
| 9.7 | Not affected |
| 9.8 | Not affected |
1 Cisco ASA Software releases prior to 9.1 and Cisco ASA Software Release 9.3 have reached end-of-software maintenance. Customers should migrate to a supported release.
Note: It is possible that certain fixed software releases for this vulnerability are affected by a bug described in Cisco Field Notice FN-64291 where a security appliance may fail to pass traffic after 213 days of uptime. Customers should review this notice before determining a course of action for addressing the vulnerability described in this advisory. The issue described in the Cisco Field Notice is not a security vulnerability.